Hi all.
I'm just here to inform you of the safety risks that not many people recognize when buying and using an RDP or VPS. Especially when buying from a less-reputable source.
However even buying from reputable sources leaves you open to potential exit-scams.
You are literally buying access to a computer that's not yours. Many people store high value information, accounts and bitcoin and even worse they leave it open 24/7. It's stupid and reckless and you should be more aware of your security. The fun thing is that they use the RDP from the beginning because they want to up their security (& anonymity ofc) but then leave a completely new and fragile system there to be targeted.
I've found a program that makes your RDP BULLETPROOF, even from local administrators. You can block any connections made trying to access your RDP, filter it by country, allow no connections at all except yourself, and deny bruteforces. You can manage working hours, ip addresses, permissions etc.
Here is the first thing I saw when i tried this out on one of the RDP's i bought of one of the main RDP sellers here on the forums.
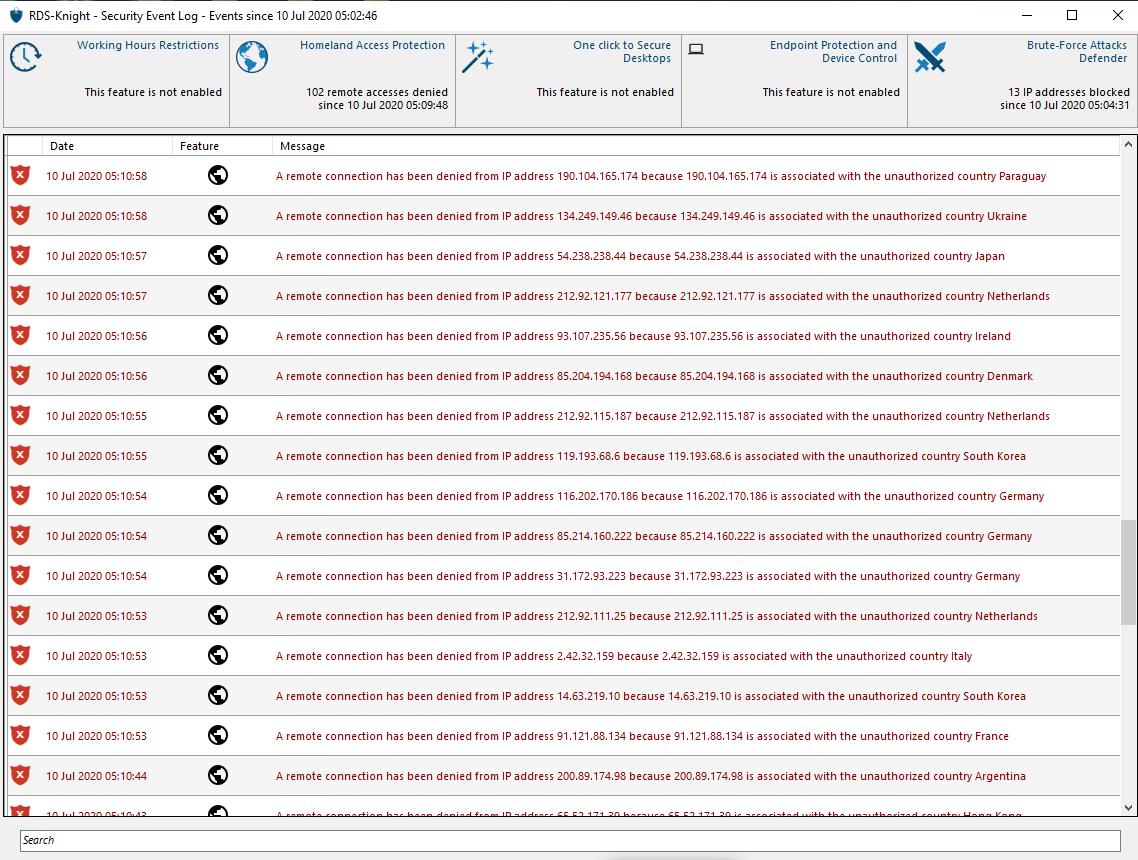
The program is called RDS-Knight and you can find the official page here -
It comes with a 15 days free trial and is priced at $50 PER SERVER using the Security Essentials and the Ultimate package being $250 A server. Would be great if we had some member of the community expertising in cracks that can get us the newest version of the ultimate package.
There are cracked versions out there but to my knowledge only older versions. Be aware of malware and do your research.
// I've looked through the forums a bit and didn't find anything related to this. Hopefully it hasn't been posted before and is something new that you all can take advantage of. //
 Sign In
Sign In Create Account
Create Account
















